SecOps influencers provide insightful commentary and content about security operations, threat detection, incident response, SOC, and other security-related issues.
The SecOps Influencers of 2023
- Jon Hencinski, Executive
- Allie Mellen, Analyst
- Farah Hawa, Creator
- Jess Dodson, Architect
- John Lambert, Executive
- Shane Brighton, Technologist
- Dana Gardner, Analyst
- Beth Pariseau, Journalist
- Sarbjeet Johal, Technologist
- Joe Panettieri, Editor
Security operations, or Secops, are processes designed to protect an organization’s information systems from malicious activity. It involves the implementation of security policies, the monitoring of system activity, and the detection and response to potential threats. Secops is critical for protecting an organization’s sensitive data and meeting compliance requirements.
In essence, Secops is a proactive approach to security that seeks to identify and address any potential risks before they can cause harm or disruption. This entails prevention measures and detection protocols that allow organizations to detect malicious actors before they can inflict damage. To achieve this goal, organizations often employ sophisticated tools such as antivirus software, firewalls, intrusion detection systems (IDS), virtual private networks (VPNs), and more. Additionally, organizations need to be trained on best security practices such as patching their systems regularly, avoiding suspicious links or downloads, implementing multi-factor authentication for user access, and more.
Secops also includes regular risk assessments to identify areas where additional security measures are needed and continual monitoring of employee use of company assets to prevent data theft or misuse. In addition to these proactive measures, organizations also need contingency plans in case something does go wrong so that they can quickly mitigate the situation with minimal disruption. This includes having backups for data in case it is lost due to an attack and incident response plans outlining the steps necessary when dealing with a breach or other form of attack.
By using these combined prevention measures through technology solutions and training users on proper security protocols while also having contingency plans in place just in case something goes wrong—Secops provides organizations with comprehensive protection against potential cyber threats.
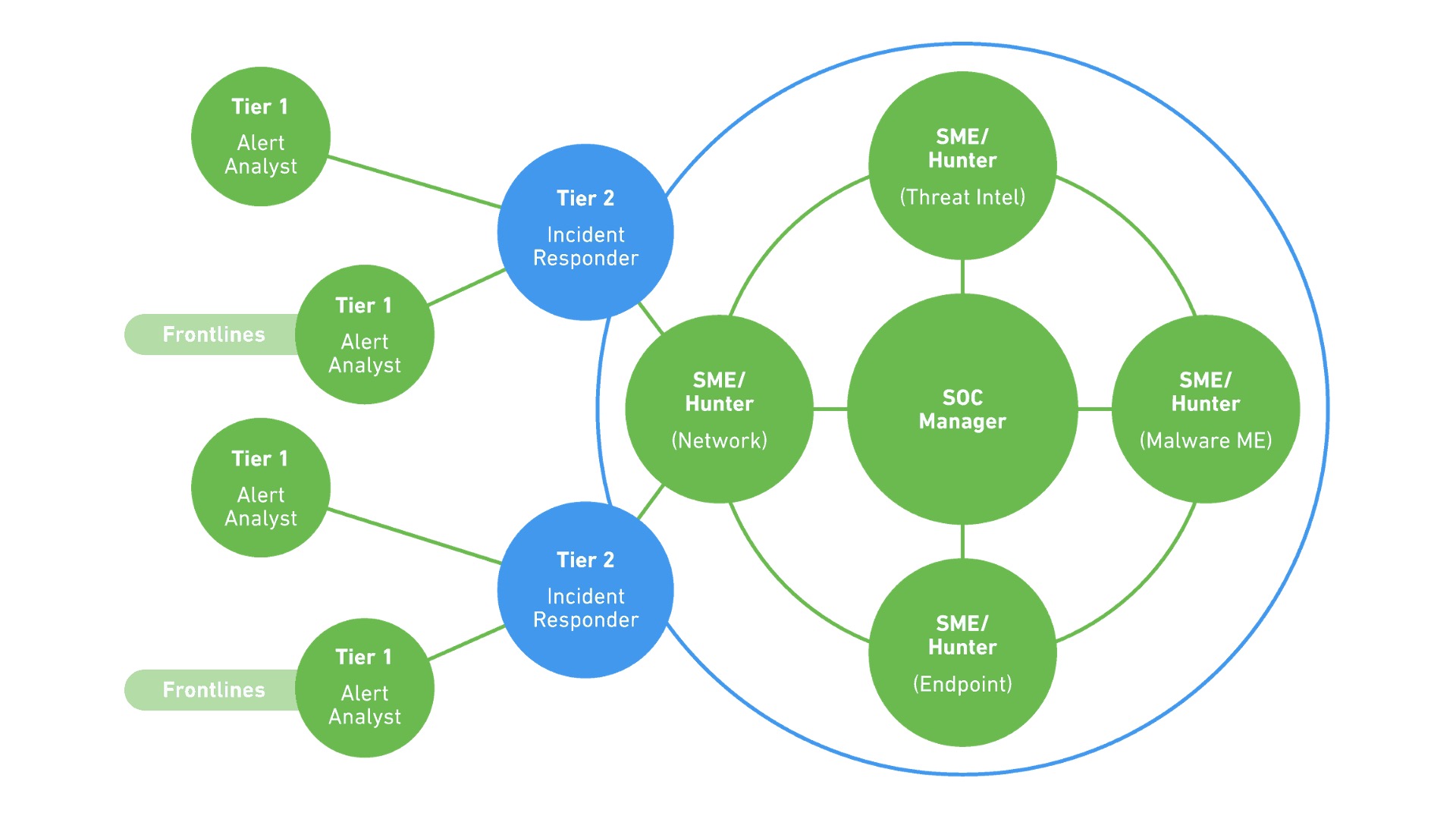
Below is a graph that shows how SecOps, SIEM, and SOC work together.
How are these SecOps influencers ranked?
For the most part, these SecOps influencers are practitioners. They are leading and working in SecOps teams in enterprise companies. They were identified using an influencer algorithm of reach, relevance, and resonance.
Reach is pretty simple. It’s how many social media followers they have across their channels. Relevance is based on topical authority and determines whether or not others consider the influencer an expert. Resonance is engagement calculated based on how many likes, comments, retweets, and links of the influencer’s content.
I like to add a layer of measurement when identifying topical influencers. It’s called reference and verifies if others have referenced the influencers. Think of it as an endorsement by the media, analyst reports, or other influencers.
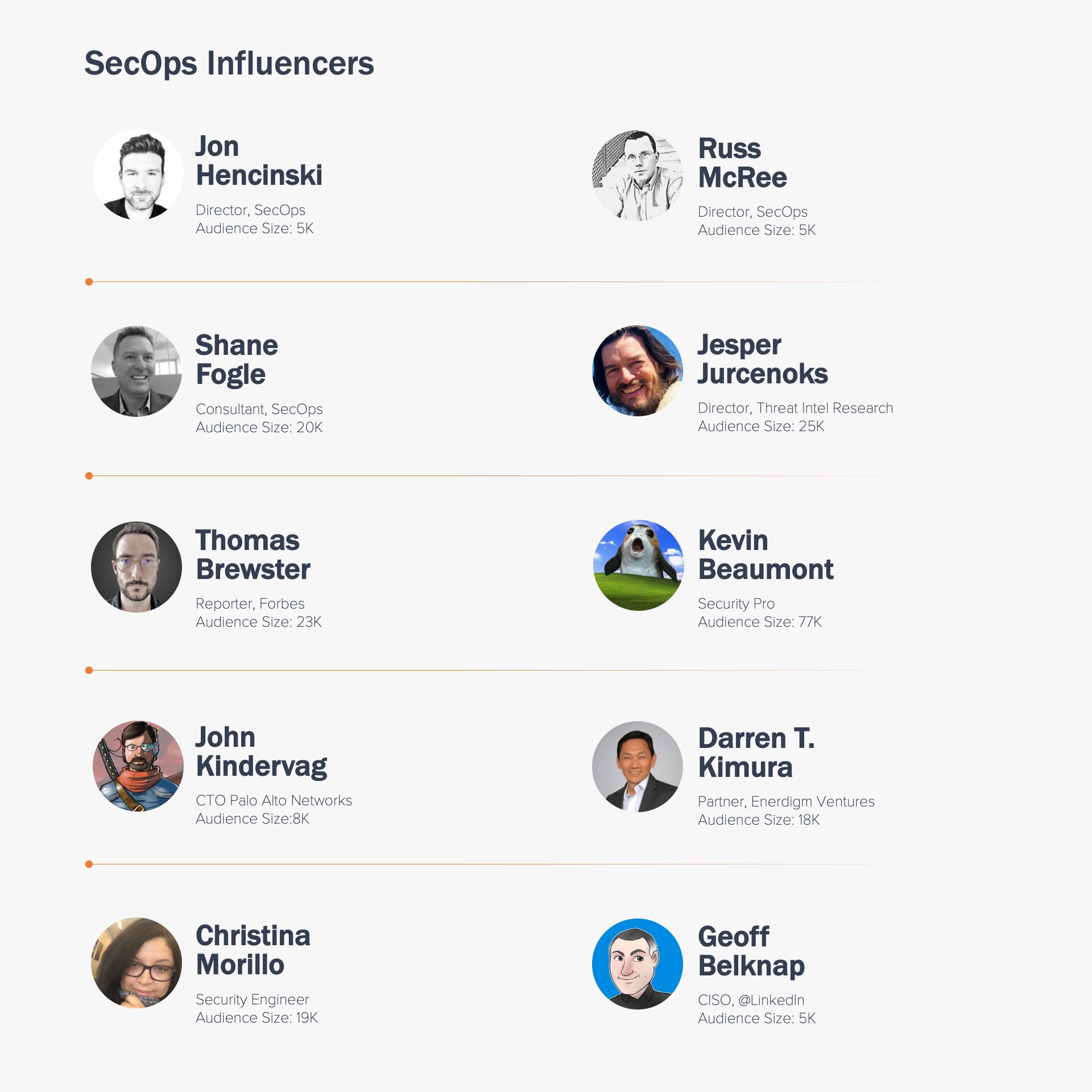
2022 SecOps Influencer List
For your convenience, here is a Twitter list of 2022 SecOps influencers below.
Using the same methodology above, we created additional technology influencer lists below. Don’t forget: Use these lists as a starting point.

Related Content
