Below is a quick analysis I did on the top cybersecurity influencers. But are they the top influencers?
Ask any tech marketer how they measure influence, and you won’t get the same answer twice. This isn’t a bad thing. Influencer intelligence should always be the first step, and there are many variables to influencer measurement. These data points can be weighted differently based on goals, objectives, the industry, and the audience you’re trying to reach.
This is one reason why I’m not a fan of influencer lists. Whenever I present influencer data to clients, I always say, “these are 10 of the top security influencers,” not “these are the top 10 security influencers.” It sounds similar, but it’s not. Influencer measurement is subjective.
Another reason I do this is because of granularity. For example, in my research, malware influencers differ from SecOps (DevSecOps, SIEM). So, categorizing influencers in the high-level topic of “security” isn’t as actionable.
I say all this because I wanted to experiment.
I Googled “top security influencers” and found several results of influencer lists. Most of them were from security software vendors (here, here, and here), a B2B tech marketing agency, Marketing Envy, and one from Onalytica — an influencer identification and management platform.
Of each list, one consistent security influencer made the top five – Brian Krebs, who owns/operates Krebs on Security, and he appeared on 4 of the five lists. Bill Brenner appeared on two different lists. Here’s a quick breakdown of each list (only the top 5 noted):
- Balbix:
- Brian Krebs – @briankrebs
- Kevin Mitnick – @kevinmitnick
- Bruce Schneier – @schneierblog
- Troy Hunt – @troyhunt
- Joseph Steinberg – @JosephSteinberg
- SaferVPN:
- Kim Zetter – @KimZetter
- Brian Krebs – @briankrebs
- Nicole Perlroth – @nicoleperlroth
- Bill Brenner – @billbrenner70
- Gene Kim – @RealGeneKim
- Data Insider:
- Adrian Sanabria – @sawaba
- Ashkan Soltani – @ashk4n
- Bill Brenner – @billbrenner70
- Brian Honan – @BrianHonan
- Brian Krebs – @briankrebs
- Marketing Envy:
- Mikko Hypponen – @mikko
- Graham Cluley – @gcluley
- Katie Moussouris – @k8em0
- Jeremiah Grossman – @jeremiahg
- Brian Krebs – @briankrebs
- Onalytica:
- Diana Kelley – @dianakelley14
- Marco Ciappelli – @MarcoCiappelli
- Rohit Ghai – @rohit_ghai
- Wendy Nather – @wendynather
- Shira Rubinoff – @Shirastweet
I’m not sure what kind of math, if any, was used in calculating these lists. It could have been just a ploy to get the attention of said influencers, which isn’t a bad idea if done right. I see this too much from the content marketing and social media industry, which bugs me. Let’s move on.
Top Cybersecurity Influencers: A Different Approach
Over the last several years, I have spent a lot of time building and analyzing audiences online. One audience, in particular, is the IT and business audience. This is important on many levels. You’ll see why.
I rarely account for influencer reach (or influencer follower count) when doing influencer research. Instead, I look for whether or not specific influencers are referenced (or mentioned) by a particular audience. In this case … a real, self-identifiable audience made up of people that matter, like security engineers, developers, architects, heads of security, etc. This, to me, should be weighted when measuring influence.
In tech, security influencers consistently reference each other on social media. This happens all the time. They tweet an article, tag another influencer, add their handle in the Tweet, flood with hashtags, and then everyone retweets. I’m not saying this is terrible, good, or whatever. It’s just what they do.
I want to know which influencers are referenced by a specific audience or group.
At Zeno, we have built an audience panel of 200,000 IT decision-makers (and growing). We can filter and mine their sharing habits, conversations, media consumption, brand affinity, top interests, etc. This is all publicly available data.
For this exercise, though, we just filtered for each influencer above. In other words, I wanted to understand if any of the above influencers are reaching more than just other influencers. I needed two questions answered:
- First, does this security audience know these influencers?
- How often is this audience sharing influencer content, if at all?
Here are the results.
The four influencers below were not mentioned by anyone from this IT security audience from June 2018 to July 2019. Most appeared on the Data Insider list and one from Onalytica. Again, I’m not saying that they aren’t influential. They just aren’t being mentioned by this particular audience panel.
- Diana Kelley
- Adrian Sanabria
- Ashkan Soltani
- Bill Brenner
The others, well … were mentioned quite a bit.
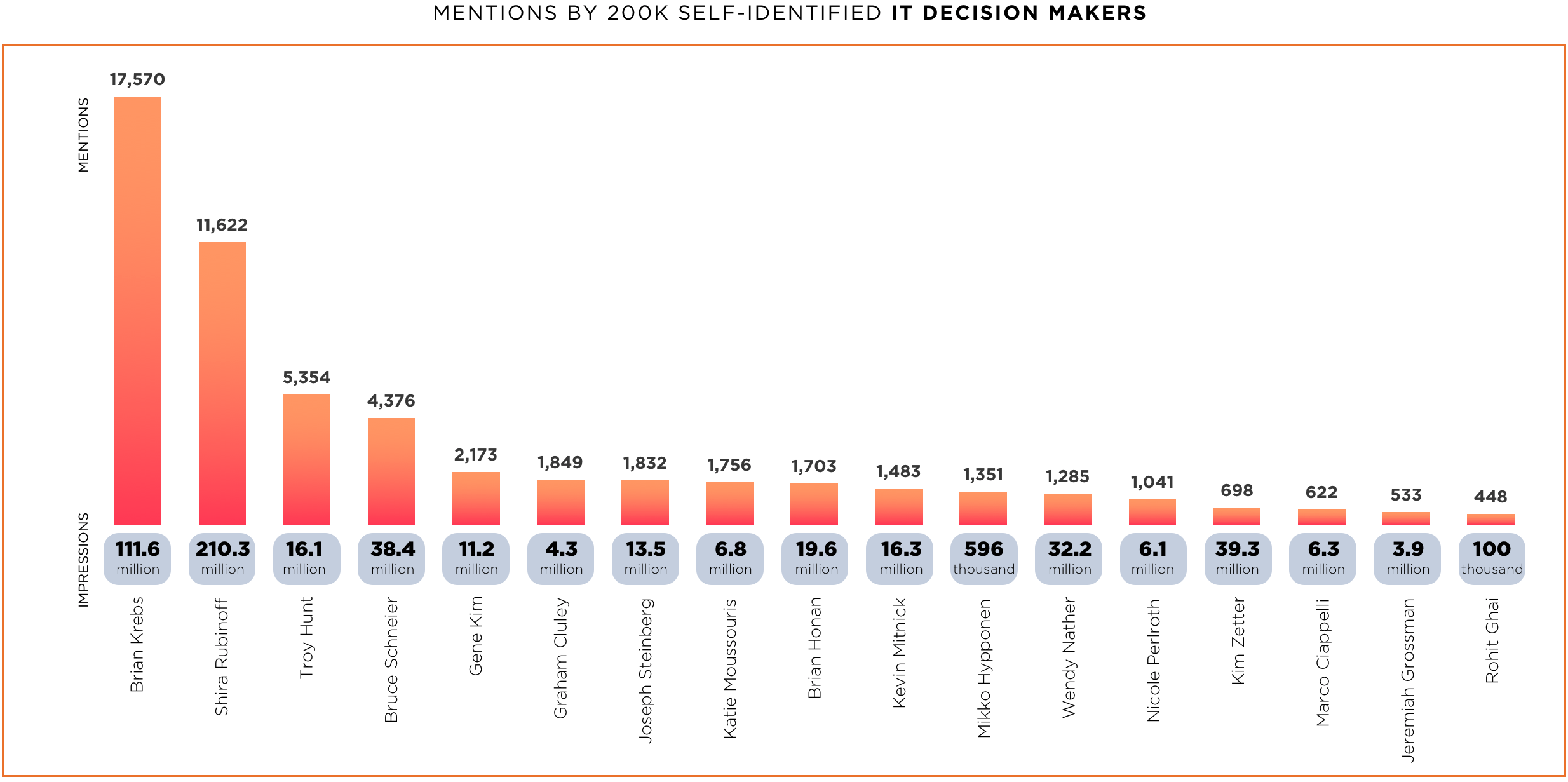
This data shows that Brian Krebs was mentioned 17,570 times during this date range and from members of this audience, resulting in ~11M impressions. Interestingly, while Shira Rubinoff was mentioned less often than Brian, those mentions resulted in almost double the impressions.
There’s more.
Of the security influencers in this analysis, the following have been mentioned or referenced in the below media publications or have published bylines:
- Brian Krebs has been mentioned in ZDNet, CNET, and Slashgear
- Troy Hunt has been mentioned in CNET, TechDirt, Sahsdot, Data Breach Today
- Bruce Schneier has been mentioned in the New York Times, TechDirt, Slashdot, Reuters, Data Breach Today
- Gene Kim has been mentioned in Computer Weekly
- Mikko Hypponen has been mention in CSO Online
Ok, so what? Let’s dig into this a little more and get some clarity.
These security influencers have been mentioned in some very reputable media publications. The next question is whether or not our security audience reads these publications and at what frequency. The CASB Gartner Magic Quadrant is a good starting point.
We cross-referenced the audience to see if they were reading and sharing content from these sites to answer this question. The data shows that they do.
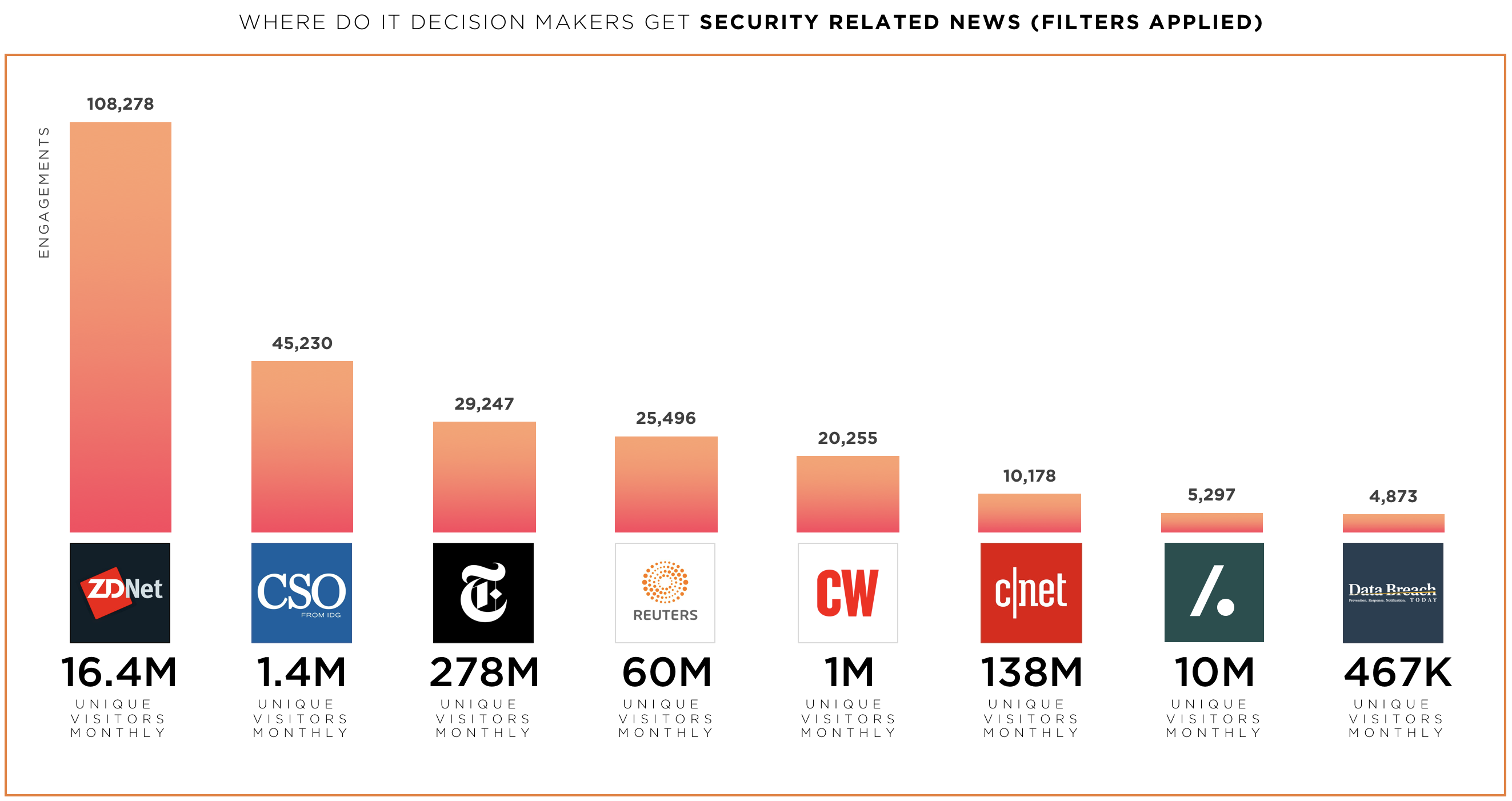
Analyzing the sites in the data set shows that our audience prefers to read ZDNet 2x more than CSO Online and 3x more than the New York Times. The engagements represent this audience’s total number of social actions (likes, comments, shares, retweets, and inbound links). Again, we only looked at the media where influencers were mentioned over the last 12 months. No other sites were considered in this part of the analysis. I’ve also added UVMs for each media publication. The data is meaningless, but it looks good.
So, it’s safe to say that our influencers could reach security audiences in those specific media publications.
A couple of notes.
- This data does not account for the volume of articles published. That’s a different slice of the data, but it’s essential. For example, if ZDNet published 10,000 articles and CSO Online published 100 articles, it could be argued that this audience may prefer CSO over ZDNet.
- Initially, this data filtering was topical based on using a security boolean. However, if we looked at artificial intelligence or digital transformation, the above media would most likely be very different. So the takeaway is that these are the top sites that security pros read when consuming security content.
- The secondary filtering was for a finite set of media sites – NY Times, ZDNet, etc. We did this because the named influencers were mentioned over the last 12 months. So the next logical question is, are other media sites more or less popular among the audience?
The answer is yes. And here they are:
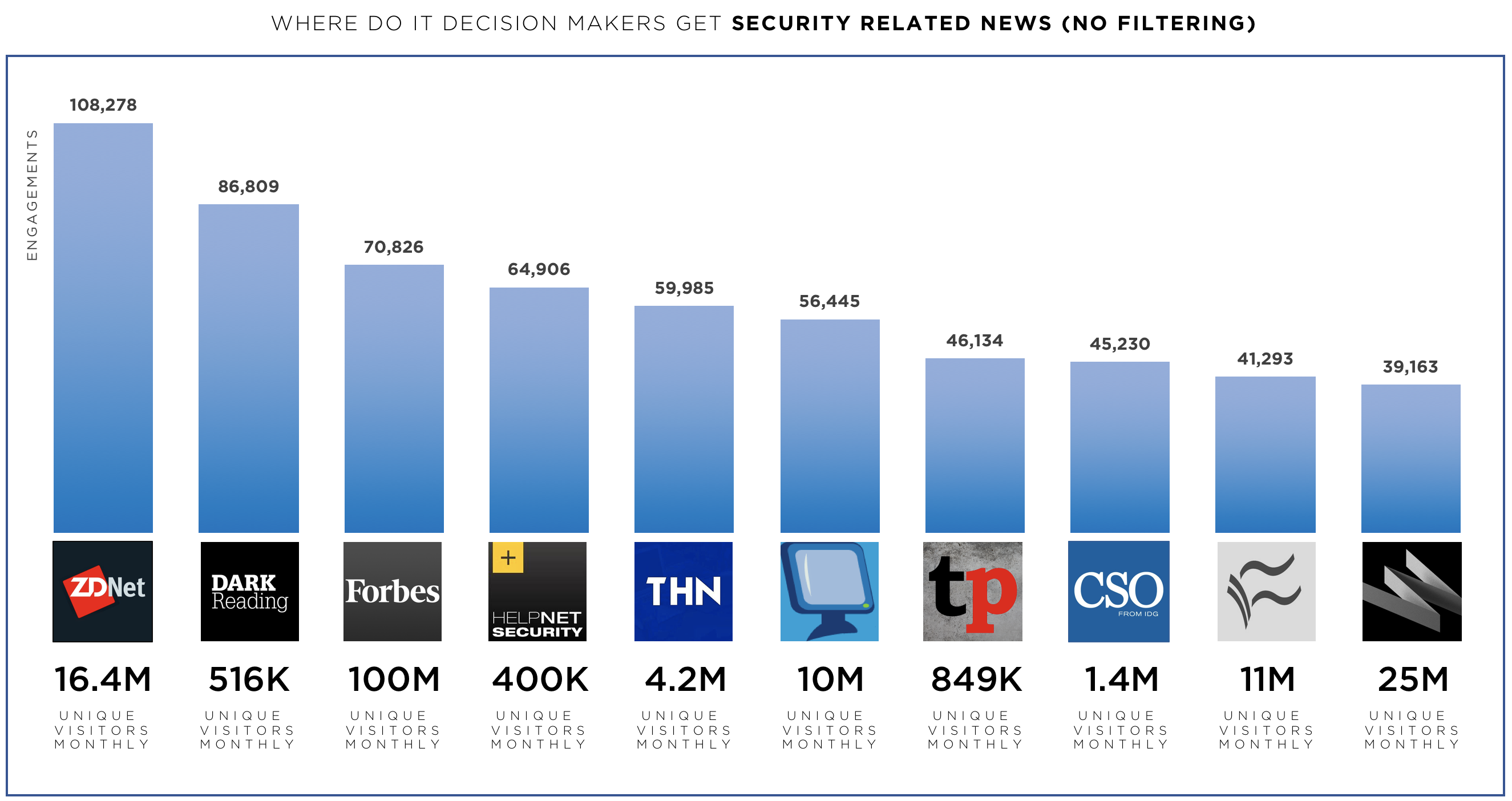
These are the top 10 media publications that security pros read when consuming security-related content, with no filtering whatsoever. You’ll notice some commonalities with the above graph, specifically that ZDNet is the most consumed media publication compared to all other security publications.
As you can see, influencer research is a subjective practice. It requires an understanding of your business, marketing goals, and KPIs. So the next time you visit a list floating around on the internet, be skeptical.
But there’s still an unanswered question. Are these the top influencers in the enterprise security space? I honestly don’t know since our data sources were based on five existing influencer lists, nothing more. So perhaps that’s the next post.
For reference. we created additional technology influencer lists below. Don’t forget: Use these lists as a starting point.

Related Content
